Facebook users are being attacked yet again. Hackers launched their latest phishing drive yesterday and successfully gathered a number of passwords from different people from its 200 million user base. The site fought against a similar phishing scam a couple of weeks ago.
Hackers managed to break into the accounts of many Facebook members and sent emails to the users friends list recommending them to click on links to fake websites.
The Fake Facebook Website
1. These fake websites were designed to look like the Facebook home page.
2. The victims were asked to login to the fake site, that actually took them to the malicious site controlled by the hackers
3. The result users unknowingly gave away their passwords.
4. The fake domains include:
* www.151.im
* www.121.im
* www.123.im
Last year, hackers spread a malicious virus called Koobface. This was sent to the user as a link in an email that looked as if it had been sent by a friend on Facebook. When the user clicked on the link, the virus was downloaded on the users computer.
The Motive
The main motive for such attacks has been identified mainly as:
1. Identify theft
2. To spread spam hawking fake pharmaceuticals and other goods to Facebook members
Damage Control
Barry Schnitt, Facebooks spokesman said that the site was in the process of cleaning up damage from the attack. Facebook was blocking compromised accounts, however, he did not say how many accounts had been compromised.
Facebook has deleted all references to the fake domains that have been identified.
Careful!
So please be extra careful. Make sure you go to the main Facebook Homepage to login to your account. It is very important that we remember NOT TO log into a page that claims to be Facebook unless the URL is www.facebook.com.
Saturday, May 23, 2009
Sunday, May 17, 2009
Lock any Folder, without any Software
Sometimes you have some data you want to save from your friends, you dont want to use any Folder lock software. Then in that case what will you do?
Well here is a simple solution. Suppose you have a folder “TEST”, and you want to lock it.
Just follow the steps and see the result.
1. Open a notepad and copy paste the code ; “ren test test.{21EC2020-3AEA-1069-A2DD-08002B30309D}”, without quotes.
2. Save this file as “loc.bat”.
3. Open notepad again and paste in the code ; “ren test.{21EC2020-3AEA-1069-A2DD-08002B30309D} test”, without quotes, and save this file as “key.bat”.
4. Just paste both these files where your folder is located. Run the LOC file and your folder will turn into Control Panel.
5. To unlock that you need to run the KEY file and everything will become back to normal.
This is very basic kind of locking, Very few people know of this. However, If you want some higher level of security for your data, you can try folder locking softwares available in the market.
Well here is a simple solution. Suppose you have a folder “TEST”, and you want to lock it.
Just follow the steps and see the result.
1. Open a notepad and copy paste the code ; “ren test test.{21EC2020-3AEA-1069-A2DD-08002B30309D}”, without quotes.
2. Save this file as “loc.bat”.
3. Open notepad again and paste in the code ; “ren test.{21EC2020-3AEA-1069-A2DD-08002B30309D} test”, without quotes, and save this file as “key.bat”.
4. Just paste both these files where your folder is located. Run the LOC file and your folder will turn into Control Panel.
5. To unlock that you need to run the KEY file and everything will become back to normal.
This is very basic kind of locking, Very few people know of this. However, If you want some higher level of security for your data, you can try folder locking softwares available in the market.
Shut down Some1 else Computer ForceFully
create a file with the extension .bat
for suppose enemy.bat
u can create this file with the help of the notepad .. and save it as .bat extension. .bat stand for batch file.
please write the following code into the enemy.bat file
shutdown -c "This Computer is effected by aman virus......." -s
insted of "this computer is effected by virus ..... " you can give ur own message...
but do not alter other attributes.
now save the file with the name you want but with extension .bat
now doubble click on this file and see magic. u can mail this file to others.
there is no way seem to abort the shut down .
but u could create a antidote for it ....
again create a file with extension .bat , for suppose anti.bat
in this file write :- shutdown -a
and save it
when u will click this file the shoutdown process will stop
for suppose enemy.bat
u can create this file with the help of the notepad .. and save it as .bat extension. .bat stand for batch file.
please write the following code into the enemy.bat file
shutdown -c "This Computer is effected by aman virus......." -s
insted of "this computer is effected by virus ..... " you can give ur own message...
but do not alter other attributes.
now save the file with the name you want but with extension .bat
now doubble click on this file and see magic. u can mail this file to others.
there is no way seem to abort the shut down .
but u could create a antidote for it ....
again create a file with extension .bat , for suppose anti.bat
in this file write :- shutdown -a
and save it
when u will click this file the shoutdown process will stop
Thursday, May 14, 2009
What's new in Windows 7?
There has been a lot written about the current Windows operating system version, Vista. Some people have liked it immensely and others can't stop detesting it. However, when the Windows 7 beta was revealed to the public last year and made available as a download, it has received very rave reviews all around.
We are starting a new series that will delve into the new and enhanced features in the next major client operating system from Microsoft. In this first of the series, we will take a broad, overall view of features that would be most visible and some that have deeper meanings for users.
The New Taskbar
The taskbar is one of the most recognizable features of Windows ever since Windows 95. Although there have been changes in each version that has come out, none have been as dramatic as the one in Win7. Now nicknamed as "SuperBar", the new Taskbar comes with a whole new set of features by itself. For instance, instead of a Quick Launch bar and a separate running tasks area, the Taskbar now combines both of these to allow "pinnable" application icons.
That is, an application can appear as an icon on the Taskbar, but when launched, the same icon now acts as the running task, saving a whole bunch of real estate on the bar. Other abilities include interactive preview thumbnails, Aero based peeking into other windows and more.
The system notification area too has got a facelift. Instead of being cluttered with a ton of application icons all vying for the limited space in this area, Windows 7 allows only 4 icons in this area. All others are available by clicking an arrow to see them.
Desktop & Explorer
There have been a number of changes made to the Desktop as well. Personalization schemes include being able to rotate your wallpapers automatically and a number of other organizational features. The Windows Sidebar is now gone, although Gadgets have not. You can now drop gadgets directly anywhere on the desktop and be able to use them.
The new "SuperBar" is larger and contains a huge number of features by itself.
Windows Explorer has introduced a new data organization feature called "Libraries". These are special "folders" that can point to a number of different folders on your system or network. For instance, the Music library can point to c:\Users \Vinod \Music, D:\Media\Music and \\homeserver \Media\Muzik. Opening the Music library lets you see all the different files across these locations in one view as if they are all in a single folder on your system.
We are starting a new series that will delve into the new and enhanced features in the next major client operating system from Microsoft. In this first of the series, we will take a broad, overall view of features that would be most visible and some that have deeper meanings for users.
The New Taskbar
The taskbar is one of the most recognizable features of Windows ever since Windows 95. Although there have been changes in each version that has come out, none have been as dramatic as the one in Win7. Now nicknamed as "SuperBar", the new Taskbar comes with a whole new set of features by itself. For instance, instead of a Quick Launch bar and a separate running tasks area, the Taskbar now combines both of these to allow "pinnable" application icons.
That is, an application can appear as an icon on the Taskbar, but when launched, the same icon now acts as the running task, saving a whole bunch of real estate on the bar. Other abilities include interactive preview thumbnails, Aero based peeking into other windows and more.
The system notification area too has got a facelift. Instead of being cluttered with a ton of application icons all vying for the limited space in this area, Windows 7 allows only 4 icons in this area. All others are available by clicking an arrow to see them.
Desktop & Explorer
There have been a number of changes made to the Desktop as well. Personalization schemes include being able to rotate your wallpapers automatically and a number of other organizational features. The Windows Sidebar is now gone, although Gadgets have not. You can now drop gadgets directly anywhere on the desktop and be able to use them.
The new "SuperBar" is larger and contains a huge number of features by itself.
Windows Explorer has introduced a new data organization feature called "Libraries". These are special "folders" that can point to a number of different folders on your system or network. For instance, the Music library can point to c:\Users \Vinod \Music, D:\Media\Music and \\homeserver \Media\Muzik. Opening the Music library lets you see all the different files across these locations in one view as if they are all in a single folder on your system.
Microsoft releases PHP SDK for MS Azure
HYDERABAD, INDIA: With the vision of 'opening' up to a large ecosystem of developers and content designers, Microsoft announced today the release of the PHP SDK for Microsoft Azure, which allows PHP developers use the Azure to develop faster.
Taking this open initiative a step further, Microsoft has also funded for interoperability with other programming languages with its Java SDK for Microsoft .NET Services and Ruby SDK for Microsoft .NET services. .NET Services essentially is .NET on the Azure Services Platform.
Vijay Rajagopalan, principal architect, Microsoft said, "We at Microsoft have realized that we have been going after only the developers who focus on enterprise-class applications, and this where the concept of Silverlight comes from. Now we realize that there is a huge breed of what I call the 'hobbyist' developers who grasp languages swiftly and contribute a small chunk of a big application, or create small applications as part of a big project. Interoperability with platforms will expose these developers to the capabilities of the cloud."
Another interesting initiative is the ability to port Silverlight on Eclipse. Now, a Silverlight developer can invoke instances or vice versa from Eclipse, making software development more pervasive and taking it to higher levels of being open.
.NET on the cloud has three important components, a Service Bus, Access Control and Work Flow. The Service Bus is an HTTP based clearing house for third party platforms and applications. If a Java application needs to interact with one in a different environment, the Bus will form the messaging bridge based on the Access Control, which takes care of the authorization, Authentication and Registration. The Work Flow component orchestrates the connection effectively.
Speaking on the commercial viability of opening up the Azure platform, Vijay said, "Microsoft follows a scale up and scale out on demand architecture, where enterprises of any size can 'instruct' Azure to manually allocate computing power, and corresponding network capabilities on demand. This will ensure that the enterprise pays for only what it uses. Anyway, its open, so programming language is not a barrier anymore for cost effective software development. The whole system is so open that Azure lets you dictate how many instances of your application should be made and for how long. We are sure to find many takers for this option."
Taking this open initiative a step further, Microsoft has also funded for interoperability with other programming languages with its Java SDK for Microsoft .NET Services and Ruby SDK for Microsoft .NET services. .NET Services essentially is .NET on the Azure Services Platform.
Vijay Rajagopalan, principal architect, Microsoft said, "We at Microsoft have realized that we have been going after only the developers who focus on enterprise-class applications, and this where the concept of Silverlight comes from. Now we realize that there is a huge breed of what I call the 'hobbyist' developers who grasp languages swiftly and contribute a small chunk of a big application, or create small applications as part of a big project. Interoperability with platforms will expose these developers to the capabilities of the cloud."
Another interesting initiative is the ability to port Silverlight on Eclipse. Now, a Silverlight developer can invoke instances or vice versa from Eclipse, making software development more pervasive and taking it to higher levels of being open.
.NET on the cloud has three important components, a Service Bus, Access Control and Work Flow. The Service Bus is an HTTP based clearing house for third party platforms and applications. If a Java application needs to interact with one in a different environment, the Bus will form the messaging bridge based on the Access Control, which takes care of the authorization, Authentication and Registration. The Work Flow component orchestrates the connection effectively.
Speaking on the commercial viability of opening up the Azure platform, Vijay said, "Microsoft follows a scale up and scale out on demand architecture, where enterprises of any size can 'instruct' Azure to manually allocate computing power, and corresponding network capabilities on demand. This will ensure that the enterprise pays for only what it uses. Anyway, its open, so programming language is not a barrier anymore for cost effective software development. The whole system is so open that Azure lets you dictate how many instances of your application should be made and for how long. We are sure to find many takers for this option."
Saturday, May 9, 2009
All COMMANDS of MS DOS!
MANY OF OUS DONT KNW ABT MSDOS COMMANDS....THIS WILL HELP YOU OUT
MSDOS RUN COMMANDS
GO TO start/run/cmd:
ADDUSERS Add or list users to/from a CSV file
ARP Address Resolution Protocol
ASSOC Change file extension associations
ASSOCIAT One step file association
AT Schedule a command to run at a later time
ATTRIB Change file attributes
BROWSTAT Get domain, browser and PDC info
CACLS Change file permissions
CALL Call one batch program from another
CD Change Directory - move to a specific Folder
CHANGE Change Terminal Server Session properties
CHKDSK Check Disk - check and repair disk problems
CHKNTFS Check the NTFS file system
CHOICE Accept keyboard input to a batch file
CIPHER Encrypt or Decrypt files/folders
CleanMgr Automated cleanup of Temp files, recycle bin
CLEARMEM Clear memory leaks
CLIP Copy STDIN to the Windows clipboard.
CLS Clear the screen
CLUSTER Windows Clustering
CMD Start a new CMD shell
COLOR Change colours of the CMD window
COMP Compare the contents of two files or sets of files
COMPACT Compress files or folders on an NTFS partition
COMPRESS Compress individual files on an NTFS partition
CON2PRT Connect or disconnect a Printer
CONVERT Convert a FAT drive to NTFS.
COPY Copy one or more files to another location
CSVDE Import or Export Active Directory data
DATE Display or set the date
Dcomcnfg DCOM Configuration Utility
DEFRAG Defragment hard drive
DEL Delete one or more files
DELPROF Delete NT user profiles
DELTREE Delete a folder and all subfolders
DevCon Device Manager Command Line Utility
DIR Display a list of files and folders
DIRUSE Display disk usage
DISKCOMP Compare the contents of two floppy disks
DISKCOPY Copy the contents of one floppy disk to another
DNSSTAT DNS Statistics
DOSKEY Edit command line, recall commands, and create macros
DSADD Add user (computer, group..) to active directoryDSQUERY List items in active directory
DSMOD Modify user (computer, group..) in active directory
ECHO Display message on screen
ENDLOCAL End localisation of environment changes in a batch file
ERASE Delete one or more files
EXIT Quit the CMD shell
EXPAND Uncompress files
EXTRACT Uncompress CAB files
FC Compare two files
FDISK Disk Format and partition
FIND Search for a text string in a file
FINDSTR Search for strings in files
FOR Conditionally perform a command several times
FORFILES Batch process multiple files
FORMAT Format a disk
FREEDISK Check free disk space (in bytes)
FSUTIL File and Volume utilities
FTP File Transfer Protocol
FTYPE Display or modify file types used in file extension associations
GLOBAL Display membership of global groups
GOTO Direct a batch program to jump to a labelled line
HELP Online Help
HFNETCHK Network Security Hotfix Checker
IF Conditionally perform a command
IFMEMBER Is the current user in an NT Workgroup
INSTSRV Install an NT Service
IPCONFIG Configure IP
KILL Remove a program from memory
LABEL Edit a disk label
LOCAL Display membership of local groups
LOGEVENT Write text to the NT event viewer.
LOGOFF Log a user off
LOGTIME Log the date and time in a file
MAPISEND Send email from the command line
MEM Display memory usage
MD Create new folders
MODE Configure a system device
MORE Display output, one screen at a time
MOUNTVOL Manage a volume mount point
MOVE Move files from one folder to another
MOVEUSER Move a user from one domain to another
MSG Send a message
MSIEXEC Microsoft Windows Installer
MSINFO Windows NT diagnostics
MSTSC Terminal Server Connection (Remote Desktop Protocol)
MUNGE Find and Replace text within file(s)
MV Copy in-use files
NET Manage network resources
NETDOM Domain Manager
NETSH Configure network protocols
NETSVC Command-line Service Controller
NBTSTAT Display networking statistics (NetBIOS over TCP/IP)
NETSTAT Display networking statistics (TCP/IP)
NOW Display the current Date and Time
NSLOOKUP Name server lookup
NTBACKUP Backup folders to tape
NTRIGHTS Edit user account rights
PATH Display or set a search path for executable files
PATHPING Trace route plus network latency and packet loss
PAUSE Suspend processing of a batch file and display a message
PERMS Show permissions for a user
PERFMON Performance Monitor
PING Test a network connection
POPD Restore the previous value of the current directory saved by PUSHD
PORTQRY Display the status of ports and services
PRINT Print a text file
PRNCNFG Display, configure or rename a printer
PRNMNGR Add, delete, list printers set the default printer
PROMPT Change the command prompt
PUSHD Save and then change the current directory
QGREP Search file(s) for lines that match a given pattern.
RASDIAL Manage RAS connections
RASPHONE Manage RAS connections
RECOVER Recover a damaged file from a defective disk.
REG Read, Set or Delete registry keys and values
REGEDIT Import or export registry settings
REGSVR32 Register or unregister a DLL
REGINI Change Registry Permissions
REM Record comments (remarks) in a batch file
REN Rename a file or files.
REPLACE Replace or update one file with another
RD Delete folder(s)
RDISK Create a Recovery Disk
RMTSHARE Share a folder or a printer
ROBOCOPY Robust File and Folder Copy
ROUTE Manipulate network routing tables
RUNAS Execute a program under a different user account
RUNDLL32 Run a DLL command (add/remove print connections)
SC Service Control
SCHTASKS Create or Edit Scheduled Tasks
SCLIST Display NT Services
ScriptIt Control GUI applications
SET Display, set, or remove environment variables
SETLOCAL Begin localisation of environment changes in a batch file
SETX Set environment variables permanently
SHARE List or edit a file share or print share
SHIFT Shift the position of replaceable parameters in a batch file
SHORTCUT Create a windows shortcut (.LNK file)
SHOWGRPS List the NT Workgroups a user has joined
SHOWMBRS List the Users who are members of a Workgroup
SHUTDOWN Shutdown the computer
SLEEP Wait for x seconds
SOON Schedule a command to run in the near future
SORT Sort input
START Start a separate window to run a specified program or command
SU Switch User
SUBINACL Edit file and folder Permissions, Ownership and Domain
SUBST Associate a path with a drive letter
TASKLIST List running applications and services
TIME Display or set the system time
TIMEOUT Delay processing of a batch file
TITLE Set the window title for a CMD.EXE session
TOUCH Change file timestamps
TRACERT Trace route to a remote host
TREE Graphical display of folder structure
TYPE Display the contents of a text file
USRSTAT List domain usernames and last login
VER Display version information
VERIFY Verify that files have been saved
VOL Display a disk label
WHERE Locate and display files in a directory tree
WHOAMI Output the current UserName and domain
WINDIFF Compare the contents of two files or sets of files
WINMSD Windows system diagnostics
WINMSDP Windows system diagnostics IIWMIC WMI Commands
XCACLS Change file permissions
XCOPY Copy files and folders
MSDOS RUN COMMANDS
GO TO start/run/cmd:
ADDUSERS Add or list users to/from a CSV file
ARP Address Resolution Protocol
ASSOC Change file extension associations
ASSOCIAT One step file association
AT Schedule a command to run at a later time
ATTRIB Change file attributes
BROWSTAT Get domain, browser and PDC info
CACLS Change file permissions
CALL Call one batch program from another
CD Change Directory - move to a specific Folder
CHANGE Change Terminal Server Session properties
CHKDSK Check Disk - check and repair disk problems
CHKNTFS Check the NTFS file system
CHOICE Accept keyboard input to a batch file
CIPHER Encrypt or Decrypt files/folders
CleanMgr Automated cleanup of Temp files, recycle bin
CLEARMEM Clear memory leaks
CLIP Copy STDIN to the Windows clipboard.
CLS Clear the screen
CLUSTER Windows Clustering
CMD Start a new CMD shell
COLOR Change colours of the CMD window
COMP Compare the contents of two files or sets of files
COMPACT Compress files or folders on an NTFS partition
COMPRESS Compress individual files on an NTFS partition
CON2PRT Connect or disconnect a Printer
CONVERT Convert a FAT drive to NTFS.
COPY Copy one or more files to another location
CSVDE Import or Export Active Directory data
DATE Display or set the date
Dcomcnfg DCOM Configuration Utility
DEFRAG Defragment hard drive
DEL Delete one or more files
DELPROF Delete NT user profiles
DELTREE Delete a folder and all subfolders
DevCon Device Manager Command Line Utility
DIR Display a list of files and folders
DIRUSE Display disk usage
DISKCOMP Compare the contents of two floppy disks
DISKCOPY Copy the contents of one floppy disk to another
DNSSTAT DNS Statistics
DOSKEY Edit command line, recall commands, and create macros
DSADD Add user (computer, group..) to active directoryDSQUERY List items in active directory
DSMOD Modify user (computer, group..) in active directory
ECHO Display message on screen
ENDLOCAL End localisation of environment changes in a batch file
ERASE Delete one or more files
EXIT Quit the CMD shell
EXPAND Uncompress files
EXTRACT Uncompress CAB files
FC Compare two files
FDISK Disk Format and partition
FIND Search for a text string in a file
FINDSTR Search for strings in files
FOR Conditionally perform a command several times
FORFILES Batch process multiple files
FORMAT Format a disk
FREEDISK Check free disk space (in bytes)
FSUTIL File and Volume utilities
FTP File Transfer Protocol
FTYPE Display or modify file types used in file extension associations
GLOBAL Display membership of global groups
GOTO Direct a batch program to jump to a labelled line
HELP Online Help
HFNETCHK Network Security Hotfix Checker
IF Conditionally perform a command
IFMEMBER Is the current user in an NT Workgroup
INSTSRV Install an NT Service
IPCONFIG Configure IP
KILL Remove a program from memory
LABEL Edit a disk label
LOCAL Display membership of local groups
LOGEVENT Write text to the NT event viewer.
LOGOFF Log a user off
LOGTIME Log the date and time in a file
MAPISEND Send email from the command line
MEM Display memory usage
MD Create new folders
MODE Configure a system device
MORE Display output, one screen at a time
MOUNTVOL Manage a volume mount point
MOVE Move files from one folder to another
MOVEUSER Move a user from one domain to another
MSG Send a message
MSIEXEC Microsoft Windows Installer
MSINFO Windows NT diagnostics
MSTSC Terminal Server Connection (Remote Desktop Protocol)
MUNGE Find and Replace text within file(s)
MV Copy in-use files
NET Manage network resources
NETDOM Domain Manager
NETSH Configure network protocols
NETSVC Command-line Service Controller
NBTSTAT Display networking statistics (NetBIOS over TCP/IP)
NETSTAT Display networking statistics (TCP/IP)
NOW Display the current Date and Time
NSLOOKUP Name server lookup
NTBACKUP Backup folders to tape
NTRIGHTS Edit user account rights
PATH Display or set a search path for executable files
PATHPING Trace route plus network latency and packet loss
PAUSE Suspend processing of a batch file and display a message
PERMS Show permissions for a user
PERFMON Performance Monitor
PING Test a network connection
POPD Restore the previous value of the current directory saved by PUSHD
PORTQRY Display the status of ports and services
PRINT Print a text file
PRNCNFG Display, configure or rename a printer
PRNMNGR Add, delete, list printers set the default printer
PROMPT Change the command prompt
PUSHD Save and then change the current directory
QGREP Search file(s) for lines that match a given pattern.
RASDIAL Manage RAS connections
RASPHONE Manage RAS connections
RECOVER Recover a damaged file from a defective disk.
REG Read, Set or Delete registry keys and values
REGEDIT Import or export registry settings
REGSVR32 Register or unregister a DLL
REGINI Change Registry Permissions
REM Record comments (remarks) in a batch file
REN Rename a file or files.
REPLACE Replace or update one file with another
RD Delete folder(s)
RDISK Create a Recovery Disk
RMTSHARE Share a folder or a printer
ROBOCOPY Robust File and Folder Copy
ROUTE Manipulate network routing tables
RUNAS Execute a program under a different user account
RUNDLL32 Run a DLL command (add/remove print connections)
SC Service Control
SCHTASKS Create or Edit Scheduled Tasks
SCLIST Display NT Services
ScriptIt Control GUI applications
SET Display, set, or remove environment variables
SETLOCAL Begin localisation of environment changes in a batch file
SETX Set environment variables permanently
SHARE List or edit a file share or print share
SHIFT Shift the position of replaceable parameters in a batch file
SHORTCUT Create a windows shortcut (.LNK file)
SHOWGRPS List the NT Workgroups a user has joined
SHOWMBRS List the Users who are members of a Workgroup
SHUTDOWN Shutdown the computer
SLEEP Wait for x seconds
SOON Schedule a command to run in the near future
SORT Sort input
START Start a separate window to run a specified program or command
SU Switch User
SUBINACL Edit file and folder Permissions, Ownership and Domain
SUBST Associate a path with a drive letter
TASKLIST List running applications and services
TIME Display or set the system time
TIMEOUT Delay processing of a batch file
TITLE Set the window title for a CMD.EXE session
TOUCH Change file timestamps
TRACERT Trace route to a remote host
TREE Graphical display of folder structure
TYPE Display the contents of a text file
USRSTAT List domain usernames and last login
VER Display version information
VERIFY Verify that files have been saved
VOL Display a disk label
WHERE Locate and display files in a directory tree
WHOAMI Output the current UserName and domain
WINDIFF Compare the contents of two files or sets of files
WINMSD Windows system diagnostics
WINMSDP Windows system diagnostics IIWMIC WMI Commands
XCACLS Change file permissions
XCOPY Copy files and folders
Firefox add-on for Better Privacy
Even if you regularly clean your history and cookies from your Firefox browser, you will end up leaving all kinds of traces behind on your machine, allowing someone else to easily track your actions online.
One of the ways to manage this problem is by using Firefox add-ons that help remove traces and cookies in your local computer. But Flash-based streaming videos, advertisements, and controls that are nearly ubiquitous on the web these days are still left behind untouched. That’s why BetterPrivacy add-on comes in handy.
BetterPrivacy is a free download and works wherever Firefox does.
What is BetterPrivacy?
* Super-Cookie Safeguard which protects from usually undeletable LSO’s (Flash-Cookies) or DOM Storage Objects.
* It blocks long term tracking on Google, YouTube, ebay and many other domains.
With the help of this add-on, you can get rid of those hidden, never expiring objects. You can set your browser to always clean your Flash cache and DOM objects automatically. However, those of you who wish to manage all cookies manually have the option to disable the automatic functions.
Click here to download your BetterPrivacy add-on.
Link: BetterPrivacyAddon
One of the ways to manage this problem is by using Firefox add-ons that help remove traces and cookies in your local computer. But Flash-based streaming videos, advertisements, and controls that are nearly ubiquitous on the web these days are still left behind untouched. That’s why BetterPrivacy add-on comes in handy.
BetterPrivacy is a free download and works wherever Firefox does.
What is BetterPrivacy?
* Super-Cookie Safeguard which protects from usually undeletable LSO’s (Flash-Cookies) or DOM Storage Objects.
* It blocks long term tracking on Google, YouTube, ebay and many other domains.
With the help of this add-on, you can get rid of those hidden, never expiring objects. You can set your browser to always clean your Flash cache and DOM objects automatically. However, those of you who wish to manage all cookies manually have the option to disable the automatic functions.
Click here to download your BetterPrivacy add-on.
Link: BetterPrivacyAddon
Thursday, May 7, 2009
Robots coming soon on Facebook
Now you could soon be chit-chatting and making friends with robots on Facbook, helping bridge the so-called “divide between humans and machine”. Yes! This sounds unreal, but it’s true.
The man behind the idea of coupling robots with social networks?
Dr. Nikolaus Mavridis!
* Research indicates that humans lose interest in robots after about a week because of their programmed behavioral patterns.
* Dr. Mavridis, along with a few other co-researchers, is looking to explore new ways to do away with the human unwillingness to stay in touch with robots.
* Researchers want to take a deeper dive into this by having humans and robots deal with the same circle of friends and a pool of shared memories.
Which means – now robots will have a Facebook profile of their own too!
The platform for exploring
* A robot that can recognize faces (which is created by Dr. Mavridis and colleagues from the Interactive Robots and Media Lab (IRML) at the University of the UAE, along with co-workers in Germany & Greece).
* This is based around a PeopleBot machine from ActivRobots, to which they have also added a range finder, touch screen and stereo camera.
* The current prototype is called “Sarah.” When the project begins, this will be swapped for a machine with the face of an Arabic scholar - Ibn Sina aka Avicenna.
Software modules for the robot
1. To help the robot recognize the faces of real people or the photographs users place of themselves on Facebook.
2. To help the robot carry on real-time conversations using a language module.
3. To help the robot maintain a database of its friends and their social relationships based on information it gets from Facebook. This social database will also keep its own Facebook profile up to date.
In a month long trial for this robot, Dr Mavridis wants to let Ibn Sina wander around IRML talking to people it meets and trying to get to know those that it does not. When it meets anyone for the first time it will check on Facebook to see if they have a profile page and use what it finds there as the starting point for a conversation.
This is the world we live in - the world of technology and innovation, where something new is happening every day, every minute. While the robot-human engagement has happened before a lot of times, but never before have we seen anything like this on a social networking site. Whether or not this will foster a meaningful “friendship” between humans and machine, can only be seen in course of time. I am quite excited to see how this research and experiment progresses.
The man behind the idea of coupling robots with social networks?
Dr. Nikolaus Mavridis!
* Research indicates that humans lose interest in robots after about a week because of their programmed behavioral patterns.
* Dr. Mavridis, along with a few other co-researchers, is looking to explore new ways to do away with the human unwillingness to stay in touch with robots.
* Researchers want to take a deeper dive into this by having humans and robots deal with the same circle of friends and a pool of shared memories.
Which means – now robots will have a Facebook profile of their own too!
The platform for exploring
* A robot that can recognize faces (which is created by Dr. Mavridis and colleagues from the Interactive Robots and Media Lab (IRML) at the University of the UAE, along with co-workers in Germany & Greece).
* This is based around a PeopleBot machine from ActivRobots, to which they have also added a range finder, touch screen and stereo camera.
* The current prototype is called “Sarah.” When the project begins, this will be swapped for a machine with the face of an Arabic scholar - Ibn Sina aka Avicenna.
Software modules for the robot
1. To help the robot recognize the faces of real people or the photographs users place of themselves on Facebook.
2. To help the robot carry on real-time conversations using a language module.
3. To help the robot maintain a database of its friends and their social relationships based on information it gets from Facebook. This social database will also keep its own Facebook profile up to date.
In a month long trial for this robot, Dr Mavridis wants to let Ibn Sina wander around IRML talking to people it meets and trying to get to know those that it does not. When it meets anyone for the first time it will check on Facebook to see if they have a profile page and use what it finds there as the starting point for a conversation.
This is the world we live in - the world of technology and innovation, where something new is happening every day, every minute. While the robot-human engagement has happened before a lot of times, but never before have we seen anything like this on a social networking site. Whether or not this will foster a meaningful “friendship” between humans and machine, can only be seen in course of time. I am quite excited to see how this research and experiment progresses.
Facebook’s NewsFeed RSS removed due to security issues
Here’s a quick update for all Facebook users. Facebook has shut down its RSS NewsFeed application.
They had recently launched a new application that converted their News feed into RSS feed that could be subscribed to and accessed outside of Facebook.
But apparently, it violated Facebook’s privacy controls, and now it’s gone.
I think in a way it’s good to know that Facebook is concerned about the user’s privacy. Letting out your friends content and updates to a public place is not the best thing to do.
Read Write Web however believes that this Facebook feature was very useful and shouldn’t have been removed. Click here to know how and why.

Facebook is yet to respond back with an official statement. We will have to wait for a little longer to get more details on this subject.
(Source: RWW)
They had recently launched a new application that converted their News feed into RSS feed that could be subscribed to and accessed outside of Facebook.
But apparently, it violated Facebook’s privacy controls, and now it’s gone.
I think in a way it’s good to know that Facebook is concerned about the user’s privacy. Letting out your friends content and updates to a public place is not the best thing to do.
Read Write Web however believes that this Facebook feature was very useful and shouldn’t have been removed. Click here to know how and why.

Facebook is yet to respond back with an official statement. We will have to wait for a little longer to get more details on this subject.
(Source: RWW)
Wednesday, May 6, 2009
Cyber criminals control 12 mn IP addresses
Cyber criminals have taken control of as many as 12 million new IP addresses since the start of 2009, a 50 per cent increase since 2008, according to the latest quarterly threat report from security technology company McAfee, Inc.
The United States is now home to the largest percentage of botnet-infected computers, hosting 18 per cent of all zombie machines, it said in a press release. Cybercriminals are building an army of infected, 'zombie' computers to recover from last November's takedown of a central spam-hosting ISP, according to the new report from McAfee Avert Labs.
"The massive expansion of these botnets provides cybercriminals with the infrastructure they need to flood the Web with malware," said Jeff Green, senior vice president of McAfee Avert Labs. "Essentially, this is cybercrime enablement."
However, the number of spams came down partly due to the November 2008 takedown of McColo Corp, said McAfee. Compared with the same quarter a year ago, spam volumes are 20 per cent lower in 2009 and 30 per cent below the third quarter of 2008, which had the highest quarterly volumes recorded to date.
But, it warned that spam quantities are expected to rise again.
Another significant finding in the report is the resurgence of the Koobface virus. The report said more than 800 new variants of the virus were discovered in March alone
Also cybercriminals are increasing their use of URL redirects and Web 2.0 sites to disguise their location, it said.
The United States is now home to the largest percentage of botnet-infected computers, hosting 18 per cent of all zombie machines, it said in a press release. Cybercriminals are building an army of infected, 'zombie' computers to recover from last November's takedown of a central spam-hosting ISP, according to the new report from McAfee Avert Labs.
"The massive expansion of these botnets provides cybercriminals with the infrastructure they need to flood the Web with malware," said Jeff Green, senior vice president of McAfee Avert Labs. "Essentially, this is cybercrime enablement."
However, the number of spams came down partly due to the November 2008 takedown of McColo Corp, said McAfee. Compared with the same quarter a year ago, spam volumes are 20 per cent lower in 2009 and 30 per cent below the third quarter of 2008, which had the highest quarterly volumes recorded to date.
But, it warned that spam quantities are expected to rise again.
Another significant finding in the report is the resurgence of the Koobface virus. The report said more than 800 new variants of the virus were discovered in March alone
Also cybercriminals are increasing their use of URL redirects and Web 2.0 sites to disguise their location, it said.
HtmlOrkut.com – Treat for Orkut Users!
HtmlOrkut is a new portal from Gaurav Dua, who runs OrkutPlus, one of the most famous blog on Orkut.
HtmlOrkut has around 2000 graphics and glitters, over 625 High quality games, over 1000 orkut themes. Many fascinating and amazing generators, exclusive widgets, ASCII arts, musical scraps and much more.
Good thing is that all above mentioned stuff can be used with other social networking sites like Facebook, Myspace, Hi5, Bebo, Tagged, Friendster etc.
There are many sites which provides stuff like this but none of them is even close to HtmlOrkut in terms of quantity and quality.
So check HtmlOrkut to add spice to your orkut life.
Update: Gigya Integration
Forgot to mention this most important part which makes using HtmlOrkut better than other sites.
Whenever you like some content which you want to post on say orkut look for Gigya form just below content. Using that form you can directly post to orkut and other social networking site right away from HtmlOrkut.
Thanks Gaurav for update.
Link: HtmlOrkut.com
HtmlOrkut has around 2000 graphics and glitters, over 625 High quality games, over 1000 orkut themes. Many fascinating and amazing generators, exclusive widgets, ASCII arts, musical scraps and much more.
Good thing is that all above mentioned stuff can be used with other social networking sites like Facebook, Myspace, Hi5, Bebo, Tagged, Friendster etc.
There are many sites which provides stuff like this but none of them is even close to HtmlOrkut in terms of quantity and quality.
So check HtmlOrkut to add spice to your orkut life.
Update: Gigya Integration
Forgot to mention this most important part which makes using HtmlOrkut better than other sites.
Whenever you like some content which you want to post on say orkut look for Gigya form just below content. Using that form you can directly post to orkut and other social networking site right away from HtmlOrkut.
Thanks Gaurav for update.
Link: HtmlOrkut.com
hi5 adds Chat to Attract Users
In a desperate attempt to attract new users, social networking site- hi5 is now adding an instant messaging service. Currently, hi5 has almost 60 million users – which is not a bad sized audience, but way less if you compare it with other social networks such as - MySpace and Facebook, with 125.7 million and 294.7 million unique visitors respectively.
A couple of months back, hi5 had added entertainment features to engage more people through casual gaming (like sports, arcade, etc). Last month it announced its partnership with PlaySpan, powering micropayments for virtual goods and premium content sold on the social network. And very recently it partnered with Paymo to power mobile payments for virtual goods.
Chat features
hi5’s chat service is quite similar to the Facebook chat. It:
* Is an instant one-on-one messaging service
* Allows you to check who are online or offline
* Runs directly within the browser of hi5
* Has the provision to changing your online status
* Allows you to write updates
* Allows you to post profile comments
* Allows you to share photos while chatting
* Allows you to express better with hi5 “star” emoticons
Although, quite slow to change, but this seems like a good move after all. The new IM feature will not be able to bring hi5 up to Facebook’s level for sure, but might just help engage more audience. Better late than never.
Link: hi5
(Source: TechCrunch)
A couple of months back, hi5 had added entertainment features to engage more people through casual gaming (like sports, arcade, etc). Last month it announced its partnership with PlaySpan, powering micropayments for virtual goods and premium content sold on the social network. And very recently it partnered with Paymo to power mobile payments for virtual goods.
Chat features
hi5’s chat service is quite similar to the Facebook chat. It:
* Is an instant one-on-one messaging service
* Allows you to check who are online or offline
* Runs directly within the browser of hi5
* Has the provision to changing your online status
* Allows you to write updates
* Allows you to post profile comments
* Allows you to share photos while chatting
* Allows you to express better with hi5 “star” emoticons
Although, quite slow to change, but this seems like a good move after all. The new IM feature will not be able to bring hi5 up to Facebook’s level for sure, but might just help engage more audience. Better late than never.
Link: hi5
(Source: TechCrunch)
BookArmy - Never read a bad book again!
This post is for all those who love reading books but often end up running out of topics. Now use BookArmy for free tips and recommendations on the kind of books you should be reading based on your very own taste.
BookArmy is a social networking website that will connect you to a range of books and authors for you to choose from, minimizing your chances of ending up reading a really bad one again.
What is BookArmy?
It is the place to:
1. Discuss books with other readers and decide what to read next
2. Write reviews for different books
3. Build reading lists of your own choice
4. Share your bookshelf with others
5. Get the best book recommendations fitting your taste
6. Read books together with your friends and family
7. Make direct contact with authors
8. See what star rating they give the books
9. Browse the reading lists of different people
10. Ask authors questions about their own writing, and even recommend titles to them.
If you wish to register
Apart from other things, you could also:
* Create a virtual bookshelf of your favorite books
* Write and share your own reviews
* Participate in the group discussions and events
* Browse books by the network’s most read, most popular, and by author.
If you dont wish to register
You could still:
* Browse through book reviews
* Look at author pages
* Check out the videos
* Read over the group and author-led discussions.
for more info visit here
http://www.bookarmy.com/cmsc/Footer/CommonQuestions.aspx
BookArmy is a social networking website that will connect you to a range of books and authors for you to choose from, minimizing your chances of ending up reading a really bad one again.
What is BookArmy?
It is the place to:
1. Discuss books with other readers and decide what to read next
2. Write reviews for different books
3. Build reading lists of your own choice
4. Share your bookshelf with others
5. Get the best book recommendations fitting your taste
6. Read books together with your friends and family
7. Make direct contact with authors
8. See what star rating they give the books
9. Browse the reading lists of different people
10. Ask authors questions about their own writing, and even recommend titles to them.
If you wish to register
Apart from other things, you could also:
* Create a virtual bookshelf of your favorite books
* Write and share your own reviews
* Participate in the group discussions and events
* Browse books by the network’s most read, most popular, and by author.
If you dont wish to register
You could still:
* Browse through book reviews
* Look at author pages
* Check out the videos
* Read over the group and author-led discussions.
for more info visit here
http://www.bookarmy.com/cmsc/Footer/CommonQuestions.aspx
Tuesday, May 5, 2009
open blocked orkut
you can use following sites to open orkut in office and school if they are blocked
http://www.orkuch.com/
http://www.power.com/Pub/Login.aspx?ReturnUrl=%2fpriv%2fpower%2fhome.aspx
http://www.mamproxy.com/
http://www.jumboproxy.net/
http://www.kproxy.com/
http://www.hastyproxy.com
http://www.1stunblocker.com
http://www.proxeasy.com
http://www.proxyboxonline.com
http://www.proxify.com
http://www.how2unblock.com
http://www.netevader.com
http://www.zerolike.com
or go threre and get about 8500 proxy and try to open the site.
http://proxy.org/cgi_proxies.shtml
http://www.orkuch.com/
http://www.power.com/Pub/Login.aspx?ReturnUrl=%2fpriv%2fpower%2fhome.aspx
http://www.mamproxy.com/
http://www.jumboproxy.net/
http://www.kproxy.com/
http://www.hastyproxy.com
http://www.1stunblocker.com
http://www.proxeasy.com
http://www.proxyboxonline.com
http://www.proxify.com
http://www.how2unblock.com
http://www.netevader.com
http://www.zerolike.com
or go threre and get about 8500 proxy and try to open the site.
http://proxy.org/cgi_proxies.shtml
Monday, May 4, 2009
Adobe Launches Major Anti-piracy Drive
Adobe India has launched one of its largest initiatives to battle software piracy working in collaboration with local law enforcement and government authorities.
Adobe said that it recently conducted 25 civil enforcement actions in six major cities across a cross-section of users within commercial institutions, the IT and BPO industry, and other organizations dealing with creative content.
Sandeep Mehrotra, Sales Director, Adobe India said, “Our first priority is to inform and excite our customers about the power of Adobe creative and business solutions. At the same time, we educate our users on Adobe licensing programs and the concept of Software Asset Management to ensure they are working within the law. Where we find flagrant violations of our intellectual property, we will take legal action against both the distribution channel and purchaser to protect our rights.”
Organizations suspected of unlawfully using software are potentially liable for both civil and criminal penalties, including payment of damages and undertaking actions to use fully licensed software only.
Each year, software companies worldwide lose over $47 billion in revenue to piracy, according to research conducted by the Business Software Alliance.
Adobe said that it recently conducted 25 civil enforcement actions in six major cities across a cross-section of users within commercial institutions, the IT and BPO industry, and other organizations dealing with creative content.
Sandeep Mehrotra, Sales Director, Adobe India said, “Our first priority is to inform and excite our customers about the power of Adobe creative and business solutions. At the same time, we educate our users on Adobe licensing programs and the concept of Software Asset Management to ensure they are working within the law. Where we find flagrant violations of our intellectual property, we will take legal action against both the distribution channel and purchaser to protect our rights.”
Organizations suspected of unlawfully using software are potentially liable for both civil and criminal penalties, including payment of damages and undertaking actions to use fully licensed software only.
Each year, software companies worldwide lose over $47 billion in revenue to piracy, according to research conducted by the Business Software Alliance.
Sunday, May 3, 2009
Free Windows 7 for a year!
Microsoft Corp
will let users use Windows 7 Release Candidate for free. Next week you could download Windows 7 and use it till 2010. This is significantly longer than the timeframe it had set for Windows Vista’s candidate releases that remained fully functional for some eight months only.
The general public can download Windows 7 starting May 5, 2009 that will not expire until June 1, 2010. MSDN and TechNet subscribers however were slated for the download on April 30. Apparently, Microsoft’s download sites for both services were overloaded.
Free Windows 7 for over a year? But why?
We don’t know yet. Microsoft hasn’t explained why. Well may be it is a marketing strategy or a genuine attempt to get users feedback.
will let users use Windows 7 Release Candidate for free. Next week you could download Windows 7 and use it till 2010. This is significantly longer than the timeframe it had set for Windows Vista’s candidate releases that remained fully functional for some eight months only.
The general public can download Windows 7 starting May 5, 2009 that will not expire until June 1, 2010. MSDN and TechNet subscribers however were slated for the download on April 30. Apparently, Microsoft’s download sites for both services were overloaded.
Free Windows 7 for over a year? But why?
We don’t know yet. Microsoft hasn’t explained why. Well may be it is a marketing strategy or a genuine attempt to get users feedback.
Categorize your Friends on Facebook
Facebook has recently updated their Friends page, giving the users more options to organize and manage their contacts. Now, you could organize hundreds of friends
into different categories making categorization and management easier for yourself. You can now divide your friends into “logical groups” like friends, relatives, college buddies, acquaintances, etc.
New Enhancements
You can…
1. Organize people into various lists. This will not show up anywhere on your profile page, but is only for own convenience.
2. Create Friend Groups and send bulk or private messages
easily.
3. Have up to 100 friend lists and up to 1,500 friends per friend list.
4. Have the same friend on multiple lists as well.
The new friends page also makes navigation simple within the friends page.
Here is the list of the the views you get now:
1. Friend Recommendations
2. Search
3. Browse by Network
4. Browse in Alphabetical Order
5. Phonebook
6. Recent Friends
7. Friend List Filters
into different categories making categorization and management easier for yourself. You can now divide your friends into “logical groups” like friends, relatives, college buddies, acquaintances, etc.
New Enhancements
You can…
1. Organize people into various lists. This will not show up anywhere on your profile page, but is only for own convenience.
2. Create Friend Groups and send bulk or private messages
easily.
3. Have up to 100 friend lists and up to 1,500 friends per friend list.
4. Have the same friend on multiple lists as well.
The new friends page also makes navigation simple within the friends page.
Here is the list of the the views you get now:
1. Friend Recommendations
2. Search
3. Browse by Network
4. Browse in Alphabetical Order
5. Phonebook
6. Recent Friends
7. Friend List Filters
Saturday, May 2, 2009
Security Problems with Google Chrome?
There was a security threat with Google’s web browser - Google Chrome. According to the Google Chrome Team, there was an error in handling URLs with a chromehtml: protocol. This allowed the attacker to run scripts of his choice on any page or enumerate files on the local disk under certain conditions.
Because of this problem, the attacker could endanger any user who browsed a malicious site using Internet Explorer and had Google Chrome installed.
As per IBM Rational Application Security Insider, this allowed a dangerous combination of new security vulnerabilities letting a malicious attacker to bypass the Same Origin Policy restrictions for any site using the victim’s Google Chrome.
The dangerous impact:
1. Cross-Site Scripting attack where the attacker could steal cookies, save form filler data, modify user-browsing experience and facilitate phishing attacks.
2. Leaking of information: from the victim’s files and directories on the local file-system.
But, the good news is that a FIX has been released: Version 1.0.154.59 of Chrome and hopefully, all the security issues revolving around Google Chrome are under control now.
(Source: GoogleChromeReleases | IBM watchfire)
Because of this problem, the attacker could endanger any user who browsed a malicious site using Internet Explorer and had Google Chrome installed.
As per IBM Rational Application Security Insider, this allowed a dangerous combination of new security vulnerabilities letting a malicious attacker to bypass the Same Origin Policy restrictions for any site using the victim’s Google Chrome.
The dangerous impact:
1. Cross-Site Scripting attack where the attacker could steal cookies, save form filler data, modify user-browsing experience and facilitate phishing attacks.
2. Leaking of information: from the victim’s files and directories on the local file-system.
But, the good news is that a FIX has been released: Version 1.0.154.59 of Chrome and hopefully, all the security issues revolving around Google Chrome are under control now.
(Source: GoogleChromeReleases | IBM watchfire)
Beware! Phishing scam on Facebook
Has anyone faced a hoax issue on Facebook yet? If you have a Facebook account, then be a little careful. There has been a major spur of phishing attacks on Facebook to steal usernames and passwords and spam your friends.
How is it being done?
Facebook’s mail system is being used by the attackers to send messages to the users, enticing them to go to - fbaction.net - a site that duplicates Facebook’s log-in screen.
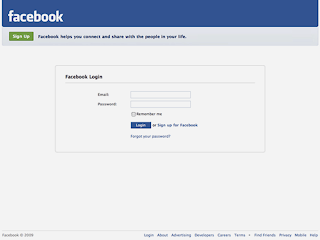
The word has been around that Facebook has blocked this URL and this has hopefully brought an end to the entire nuisance.
Better safe than sorry…
It is still very important that we REMEMBER NOT TO LOG into a page that claims to be “Facebook” unless the URL is www.facebook.com. Wouldn’t hurt being just a little extra-cautious!
(Source: allFacebook)
How is it being done?
Facebook’s mail system is being used by the attackers to send messages to the users, enticing them to go to - fbaction.net - a site that duplicates Facebook’s log-in screen.

The word has been around that Facebook has blocked this URL and this has hopefully brought an end to the entire nuisance.
Better safe than sorry…
It is still very important that we REMEMBER NOT TO LOG into a page that claims to be “Facebook” unless the URL is www.facebook.com. Wouldn’t hurt being just a little extra-cautious!
(Source: allFacebook)
Google Web Search in your Gmail
Google’s got something new in their labs yet again. This time it’s a cool feature that adds the Google search box right in your Gmail inbox. A sigh of relief! This could make life online so much more simpler!
Wonder what took them so long to come up with this?
Now, there is no need to leave your inbox to search for something online while chatting or writing an email, toggle between windows, and waste time.
How does this feature work?
* Type your search and begin searching.
* Your search results will display in something that appears to be a bigger version of a chat window, at the bottom of your screen.
* Click on the search results to read more (which will open in a new tab).
* Once you’ve found what you want, hover your mouse over the search result back in your Gmail window and you will see a pull-down menu with some options like:
- Send result while your composing email
- Reply result while chatting with someone

Enabling the feature
Just follow some simple steps below:
1. Login to your Gmail account
2. Go to the Labs tab under Settings
3. Scroll down to turn on the ‘Google Search’
4. Hit ‘Save Changes’ button
Problem solved! Try it out.
(Source: Gmail blog)
Wonder what took them so long to come up with this?
Now, there is no need to leave your inbox to search for something online while chatting or writing an email, toggle between windows, and waste time.
How does this feature work?
* Type your search and begin searching.
* Your search results will display in something that appears to be a bigger version of a chat window, at the bottom of your screen.
* Click on the search results to read more (which will open in a new tab).
* Once you’ve found what you want, hover your mouse over the search result back in your Gmail window and you will see a pull-down menu with some options like:
- Send result while your composing email
- Reply result while chatting with someone

Enabling the feature
Just follow some simple steps below:
1. Login to your Gmail account
2. Go to the Labs tab under Settings
3. Scroll down to turn on the ‘Google Search’
4. Hit ‘Save Changes’ button
Problem solved! Try it out.
(Source: Gmail blog)
Extra Emoji brings over 1000 emoticons to Gmail
A picture’s worth a thousand words. And it gets better when you have more than a thousand to choose from! With Gmail’s new Extra Emoji Icons, you can add more than 1000 emoticons in your emails.
Good news - Now you get a chance to express better without words.
Bad news - Now you spend ages wondering which emoticon to use when and where!
All these extra emoticons come from the so called “secret underground labs” of some top Japanese mobile carriers. Of course, Gmail has taken the permission to use them.
The icons are divided into 13 different categories, the first two being the standard ones from Gmail. Some of the new stuff includes animals, various road signs, national flags, and animated icons.
Enable your extra Emoji icons:
Just follow the simple steps below:
1. Login to your Gmail account
2. Go to the ‘Labs’ tab under Settings
3. Scroll down to the ‘Extra Emoji’ option
4. Check the ‘Enable’ box
5. Hit ‘Save Changes’ button
Bingo! You got it…
from gmail blog
Good news - Now you get a chance to express better without words.
Bad news - Now you spend ages wondering which emoticon to use when and where!
All these extra emoticons come from the so called “secret underground labs” of some top Japanese mobile carriers. Of course, Gmail has taken the permission to use them.
The icons are divided into 13 different categories, the first two being the standard ones from Gmail. Some of the new stuff includes animals, various road signs, national flags, and animated icons.
Enable your extra Emoji icons:
Just follow the simple steps below:
1. Login to your Gmail account
2. Go to the ‘Labs’ tab under Settings
3. Scroll down to the ‘Extra Emoji’ option
4. Check the ‘Enable’ box
5. Hit ‘Save Changes’ button
Bingo! You got it…
from gmail blog
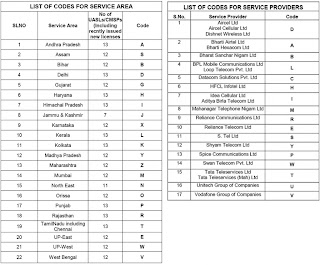
What do the codes in your SMS mean?
Have you ever received an SMS from your bank, service provider, or a company, that has been prefixed with codes? For example: An SMS from ICICI Bank that reads: IZ-ICICIBANK. Ever wondered what these codes really mean?
Telecom Regulatory Authority of India (TRAI) introduced these codes in order to curb bulk SMS providers from unsolicited commercial communication. Now that these codes are implemented, the sender can be traced, if necessary, as these codes reveal the location, the name of the company and the service provider.
This is how the code should look like:
XY-name of the company
X = Code of the service provider
Y = Location
Which means, IZ-ICICIBANK would be:
I = Idea Cellular (service provider)
Z = Maharashtra (location)
A list of Service Provider codes & Service Area codes:
Telecom Regulatory Authority of India (TRAI) introduced these codes in order to curb bulk SMS providers from unsolicited commercial communication. Now that these codes are implemented, the sender can be traced, if necessary, as these codes reveal the location, the name of the company and the service provider.
This is how the code should look like:
XY-name of the company
X = Code of the service provider
Y = Location
Which means, IZ-ICICIBANK would be:
I = Idea Cellular (service provider)
Z = Maharashtra (location)
A list of Service Provider codes & Service Area codes:

Subscribe to:
Posts (Atom)


